Information Security Management
NSK’s Approach
The use of digital technology is expanding across an increasingly wide range of fields. At the same time, the volume of information and data is also increasing dramatically with the forms in which it is held and used continuing to diversify. In this business environment, in addition to the risks associated with information leaks and violations of laws due to the improper handling of information, there is also a higher risk of increasingly sophisticated cyberattacks, which could bring supply chain operations to a halt. Positioning information security management as one of its important management tasks, the NSK Group has established the NSK Group Basic Policy on Information Security and is working to reduce a variety of risks while strengthening its response to relevant laws and regulations. Moreover, we are promoting initiatives for more robust mechanisms and organizational structures, such as network countermeasures, against increasingly sophisticated cyberattacks.
◆Basic Policy and Management Standards and Rules
The NSK Group has established a basic information security policy and put in place subordinate rules and regulations. We review and expand this policy, as well as rules and regulations, in line with the enforcement and revision of statutory and regulatory requirements and changes in our operating environment. Moreover, we are working to ensure that information security rules and risk countermeasures are implemented throughout the organization via increased awareness, development, and education, as well as periodic checks on the status of their penetration. These rules and regulations apply to all personnel who handle information within NSK Group companies, including officers, employees, and temporary staff. Furthermore, we require that appropriate information security measures are in place whenever confidential information is shared with third parties. These measures include clearly defining information security requirements through contractual agreements.
Major Information Security-Related Regulations
| NSK Group Basic Policy on Information Security | This policy sets out the objectives for the NSK Group’s information security (information security initiatives, handling of information assets, compliance with laws, regulations, and contracts, as well as education and continuous improvement). NSK Group Basic Policy on Information Security |
|---|---|
| NSK Group Information Security Management Standards | As the top information security directives in the NSK Group, these standards outline the principles for bringing the levels of information security management across the Group up to the same high standard. |
| NSK Group Information Security Procedural Standards | These rules stipulate measures to protect information assets, such as proper methods for handling information assets that need to be adopted across the NSK Group. |
System
◆Information Security Management System (ISMS)
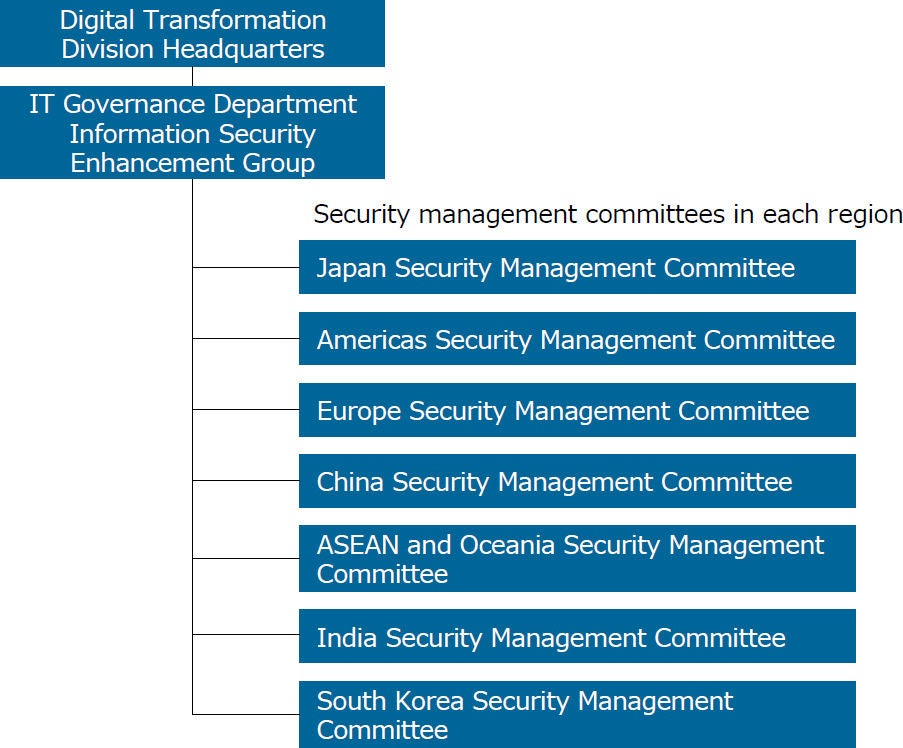
The NSK Group is enhancing its managerial resources with the power of digital technology and continuously transforming its business. This is a key priority in our Mid-Term Management Plan 2026, MTP 2026. We established the Information Security Division (IT Governance Department, Information Security Enhancement Group) under the Digital Transformation Division Headquarters at NSK Ltd., the Group headquarters, to enable the safe use of digital technology and to globally deploy information security enhancement measures that take into account the relationship between digital technology and cybersecurity. As of April 2025, the person responsible for executing information security initiatives across the NSK Group is the Head of the Digital Transformation Division Headquarters (Operating Executive). Moreover, information security-related risks are supervised under the Corporate Risk Management System and are reviewed and discussed by the Board of Directors as an issue that concerns the entire group. The Information Security Division regularly holds global meetings, working in cooperation with information security management committees in Japan, the Americas, Europe, China, ASEAN and Oceania, India, and South Korea. NSK is working to improve the information security management level of the entire NSK Group, and to plan and implement information security measures.
Furthermore, NSK has established a CSIRT* organization to quickly and appropriately respond to cyberattacks, aimed at preventing the spread of damage and facilitating swift recovery. NSK is also a member of the Nippon CSIRT Association.
* CSIRT is an abbreviation for Computer Security Incident Response Team, an organization that rapidly responds to computer security incidents.
Targets and Performance
◆Mid-Term Management Plan 2026 (MTP2026) Targets, with Targets and Performance for Each Fiscal Year
| Policy |
| |||
|---|---|---|---|---|
| MTP2026 | Targets |
|
|
|
| FY2024 | Targets |
|
|
|
| Performance |
|
|
| |
| FY2025 | Targets |
|
|
|
Initiatives
◆Enhancing Information Security Management
By utilizing globally adopted guidelines and frameworks (NIST Cyber Security Framework 2.0, CIS Controls, etc.) developed by professional cybersecurity organizations, NSK is forging a balanced approach to information security management in the context of people and organizations, processes, and technologies, while incorporating the concept of cyber resilience and working to strengthen these initiatives.
Status of Security Certifications
NSK has established a PDCA cycle for its information security management system, which includes periodic inventory and risk assessments (internal audits) of information assets and develop plans to handle and mitigate identified risks. As a result, based on demands from customers, NSK Group companies in Europe, China, and Japan acquired TISAX,* a security certification widely adopted in Germany’s automobile industry.
* Trusted Information Security Assessment Exchange (TISAX): A corporate assessment and certification system based on the VDA Information Security Assessment (VDA ISA) framework developed by the German Association of the Automotive Industry (VDA).
Enhancing Incident Response Capabilities
We are advancing technical measures to detect suspicious activities and security threats on information devices and networks. Information about detected incidents is analyzed by the Security Operations Center,*1 which then implements countermeasures. With this structure, we have established mechanisms for swiftly responding to security incidents. In addition, vulnerabilities that affect the entire NSK Group are monitored utilizing security rating services*2 and attack surface management (ASM) tools.*3
In view of the significant impact of recent security incidents on the supply chains of other companies, we also carry out information security inspections at suppliers and strive to enhance their security level. Efforts are also underway to enhance the incident response structure at NSK plants to enable not only an IT response, but an OT*4 response to incidents, as well.
*1 Security Operations Center is an organization dedicated to detecting, analyzing, and taking countermeasures to cybersecurity threats.
*2 Security rating services quantify a company’s security measures to provide ratings that are useful in external and internal risk assessment and the formulation of countermeasures.
*3 Attack surface management is a series of processes executed to discover IT assets that are accessible from outside the organization (via the Internet) and to continuously identify and assess the vulnerabilities and other risks they present.
*4 Operational technology (OT) consists of plant and other facility control systems. Whereas IT deals specifically with information, OT is considered unique in that it interacts with the physical environment.
Training and Countermeasures Against Cyberattack
NSK conducts annual drills simulating incidents triggered by cyberattack. In FY2024, we participated in the NISC/NCA collaborative drill* held by the Nippon CSIRT Association to verify whether our response structure would function effectively in the event of an actual incident. We also collaborate with regional system management departments to provide training on targeted attack emails to all employees who use a PC. Incident response drills at plants simulate attacks that have taken down internal plant systems and OT systems. We evaluate our incident response procedures to ensure production continuity in the event of an emergency and improve them based on identified issues.
* NISC/NCA collaborative drills are cyber drills executed jointly by the National center of Incident readiness and Strategy for Cybersecurity (NISC) and Nippon CSIRT Association (NCA). NISC conducts an annual all-sectoral critical infrastructure provider drill (cybersecurity tabletop exercise) every December for NCA members.
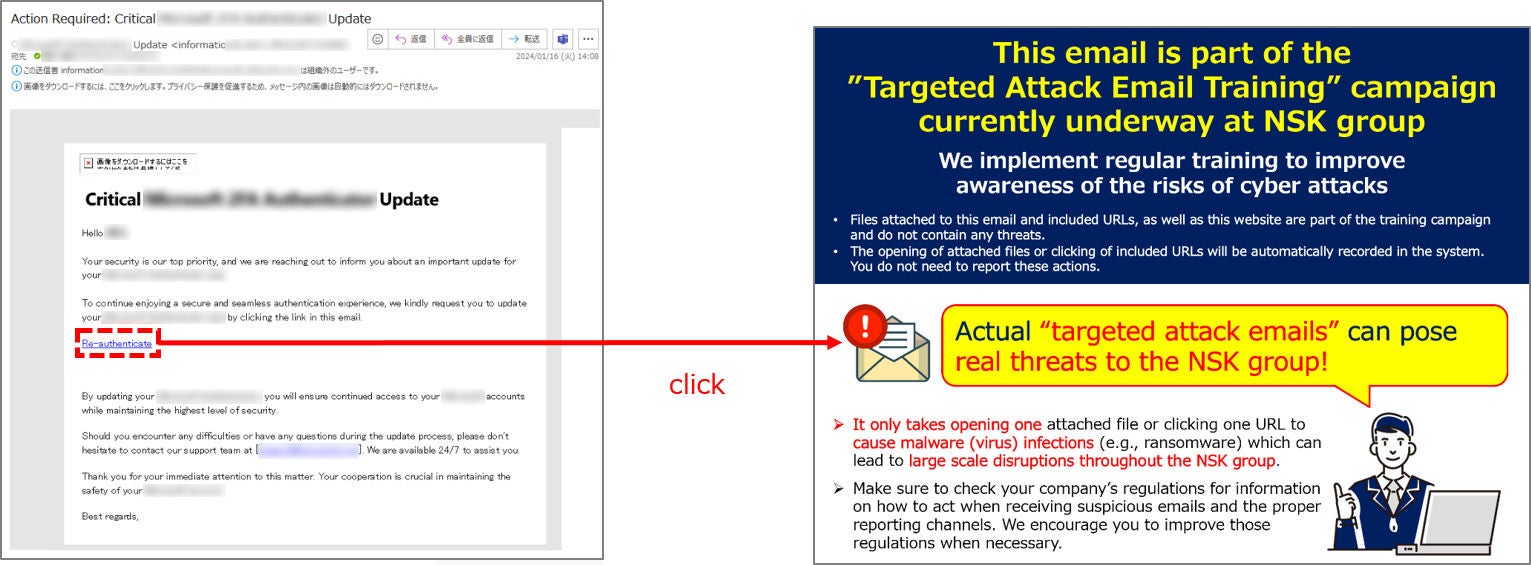
Image from Targeted Attack Email Training
Educational content is displayed to employees who do not handle a suspicious email properly, in order to help employees thoroughly understand the appropriate actions to be taken.
◆Raising Information Security Awareness
Prevention of Information Leaks and Information Security Education
The NSK Group has established rules for classifying and appropriately handling information according to the confidentiality level of information assets, paying close attention to the handling of confidential information and striving to prevent information leaks. As part of our education and awareness efforts, we conduct regular e-learning programs for employees around the world. Furthermore, we provide training by employee categories, such as officers and the system management department members, as well as training at the time of hiring or before being posted overseas.
Information Security Desk
The NSK Group has an internal system for disseminating security information and receiving security incident reports. We also have an escalation process to ensure that appropriate procedures are carried out when such reports are made.